Identity Theft Risk Assessment Template
Itap uncovers the identity attributes most vulnerable to theft assesses.
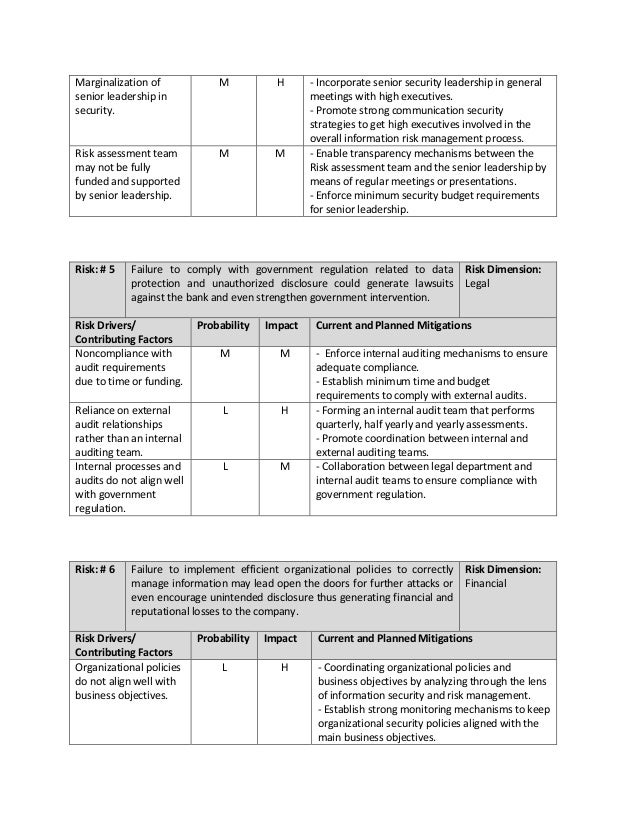
Identity theft risk assessment template. A customer is a person that has a covered account with a financial institution. This template is an optional guide for firms to assist them in fulfilling their requirements under securities and exchange commission sec regulation s id. Identity theft prevention program itpp under the ftc fact act red flags rule. This is a pretty common requirement that can seem like an insurmountable obstacle since most people are not trained on how to perform a risk assessment or they lack a simple tool that is comprehensive enough to meet their needs.
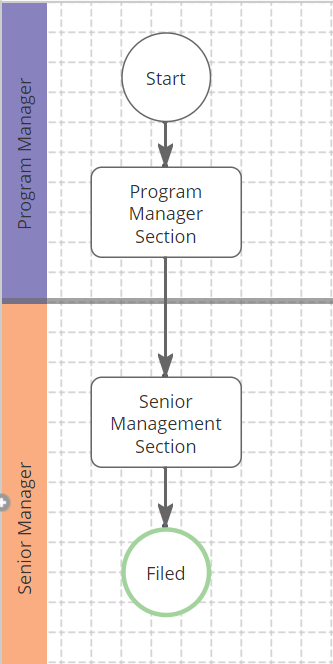
The second section of the template is essentially an identity theft prevention program checklist that requires the business to fill in the procedural and administrative blanks. Effectiveness of policies and procedures. Identify training procedures and the effectiveness of the procedures for identifying and preventing identity theft. The regulations require o financial institutions and creditors to implement a written identity theft prevention program.
Of the financial institution from identity theft including financial operational compliance reputation or litigation risks. If identity theft isnt a big risk in your business complying with the rule is simple and straightforward. Identity theft red flags red flags rule which requires specified firms to create a written identity theft prevention program itpp designed to identify detect and respond to red flagspatterns practices or specific activitiesthat could indicate identity theft. Cybersecurity risk assessment template.
Anyone using the ftc template should recognize that the template is a guide for performing the assessments required by the federal regulations it does not excuse low risk businesses from compliance. Our firms policy is to protect our customers and their accounts from identity theft and to comply with the ftcs red flags rule. Identity theft means a fraud committed or attempted using the identifying information of another person without authority. For example if the risk of identity theft is low your program might focus on how to respond if you are notified say by a customer or a law enforcement officer that someones identity was misused at your business.
State your firms objectives for your itpp. Need to perform an information security risk assessment.